ISO 27001 is an international standard for Information Security Management Systems (ISMS). This standard provides a systematic approach for companies to manage sensitive company information and ensure its confidentiality, integrity, and availability. An ISMS is a comprehensive security framework designed to protect an organization’s information assets from various threats and vulnerabilities. This framework is not limited to only digital data but also includes physical and human-related aspects of security.
The guidelines of ISO 27001 outline a set of requirements and best practices for establishing, implementing, maintaining, and continuously improving an effective ISMS. It involves a risk-based approach, where organizations identify and assess potential security risks and take appropriate measures to mitigate them. The standard covers a wide range of security controls, including data protection, access controls, incident management, employee awareness, and more. By following these guidelines, organizations can proactively manage security risks and respond effectively to security incidents.
Quick and easy ISO 27001 vulnerability compliance
It can be hard for many companies to keep up and maintain their cybersecurity in the rapidly growing world of web technologies. Nowadays, companies not only need to protect their external assets such as their websites and applications but also their internal ones such as their cloud and on-premises systems as well. Many of the older and well-loved vulnerability scanners are not able to scan large and complex assets with accuracy and efficiency.
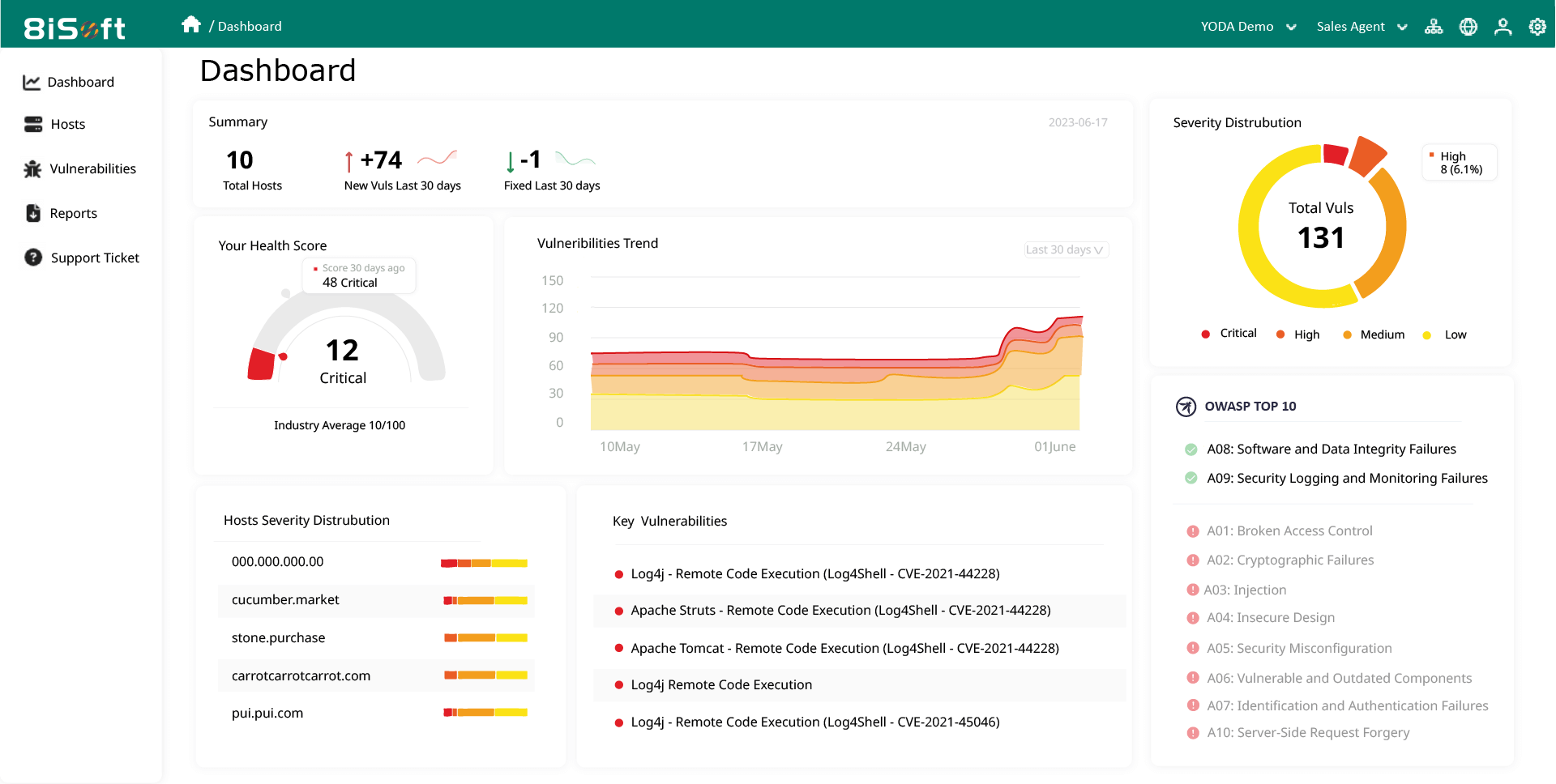
With our Discovery, Remediation, and Improvement (DRI) framework, 8iSoft Yoda is able to efficiently detect and manage vulnerabilities within your network infrastructure. Users can customize their ISO 27001 vulnerability compliance scan schedule using 8iSoft, and with the system’s wide scope of defense that covers both internal and external assets, this ensures that ISO 27001 vulnerabilities are found. 8iSoft Yoda is 100% ISO 27001 compliant and certified and strives to help firms create and establish the best practices to attaining and keeping their ISO 27001.
Audit ready compliance reports and SME validated AI-based solution steps
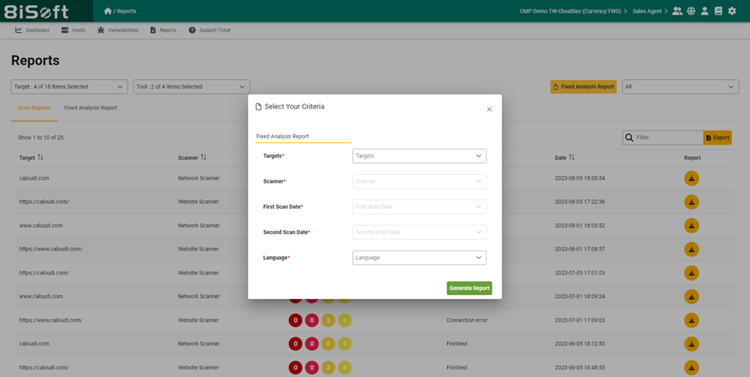
Users can use 8iSoft Yoda’s report feature to generate a comprehensive overview of the security vulnerabilities present in their company’s infrastructure.
These reports not only help businesses identify and prioritize their security weaknesses but also provide step-by-step instructions for each risk. 8iSoft Yoda offers multiple remediation plans for cybersecurity risks detected to help users understand how their identified risks and vulnerabilities can be fixed. With priority ranking given in the reports, teams will be able to find and figure out the urgency of the problems and delegate their resources accordingly. This aligns with ISO 27001’s risk-based approach to security. Through these reports, companies can also maintain a record of their actions and their remediation efforts, once again complying with ISO 27001.
8iSoft Yoda offers a great partner for your firm in maintaining and achieving ISO 27001. Through scheduled scans, vulnerability reports, and remediation plans, 8iSoft Yoda does the brunt of the work in protecting your company. By trusting 8iSoft Yoda, companies can easily strengthen their network security and comply with ISO 27001 guidelines.
ISO 27001 and Its 8th Domain
ISO 27001 (International Organization for Standardization) is an information security standard created by the globally recognized International Organization for Standardization that sets international standards for various industries to ensure consistency, safety, and quality. The primary objective of ISO 27001 is to assist organizations in safeguarding their vital information assets and adhering to relevant legal and regulatory obligations. To maintain ISO compliance, it is crucial for every individual in the organization to adhere to the established guidelines.
ISO 27001 covers 14 domains with each one detailing different guidelines for each domain to achieve optimal security in a company. For this article, we will be focusing on domain 8. If you want to learn more about the 14 domains of ISO 27001, please check out this article here “Navigating the 14 Domains of ISO 27001”.
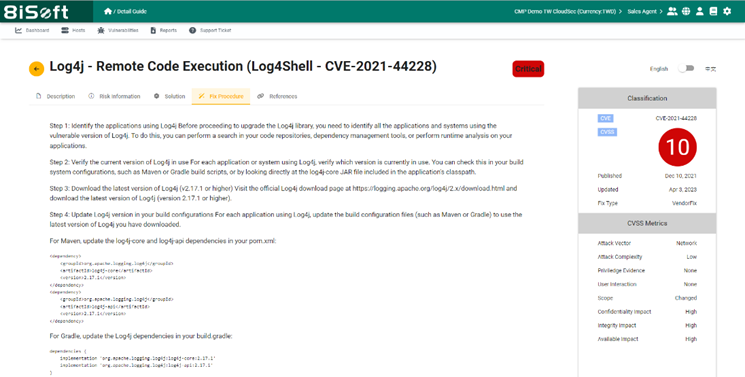
The 8th phase of ISO 27001 is “Operations Security”. This section encompasses controls related to the secure operation and management of information processing facilities and resources.” To fulfill this part of the ISO guidelines, it is recommended each employee is obligated to audit their personal devices and work devices to uphold ISO 27001 values to maintain the confidentiality and integrity of the company’s information assets.
Standard Templates from ISO
However, contrary to common belief, ISO does not provide ready-made, one-size-fits-all templates for achieving compliance. Instead, ISO standards only outline requirements and best practices that companies must meet, leaving the implementation specifics up to individual organizations. This open-ended approach allows businesses to tailor their processes to their unique operations and contexts, but also leaves many firms unsure of where to start.
Our first recommendation is to ensure that each person’s computer in a company is ISO compliant. To do so, it is necessary to create a tailored approach or checklist for every individual at the company to follow. At 8iSoft, we have been able to create and curate a checklist that has allowed us to continuously uphold our own ISO 27001 certification. Our employees use this checklist to routinely audit their personal devices and ensure that their cybersecurity is safeguarded.

